First Principle of Cybersecurity
What should be the first principle of cybersecurity within any organization? The answer is simple, yet often overlooked: Reduce the probability of material impact to my organization due to a cyber event.
What is one way to help achieve this first principle? Understanding the most vulnerable points within your organization, and which areas of your organization pose the most risk. To do this, you need to have knowledge of where in your organization you are susceptible to an attacker gaining unwanted entry to your organization’s systems or network environments.
Attack Surface
The term Attack Surface refers to any entry points that may allow for an attacker to gain unauthorized entry to your organizations systems, accounts, and networks.
With the increased shift to working from home (and other external locations) due to the Covid-19 pandemic, the Attack Surface has spread greatly over the recent year(s). The following diagram will illustrate the wide range of susceptible points within any standard organization:
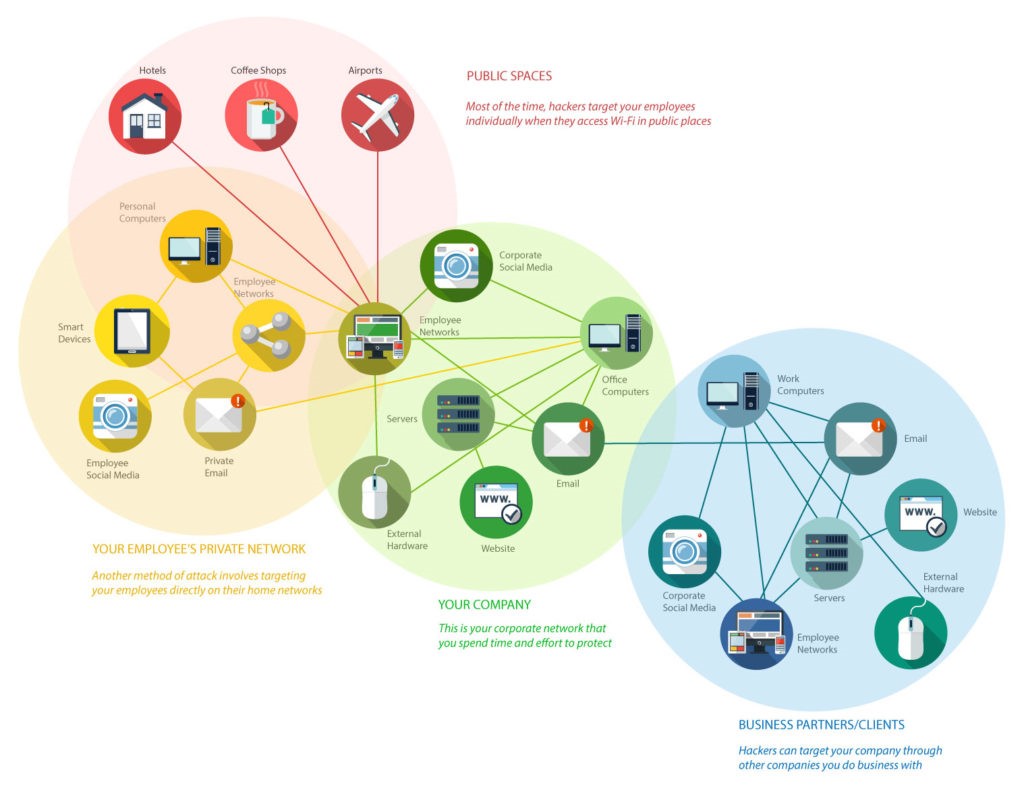
Source: https://graquantum.com/cyber-basics-cyber-attack-surface/
Attack Surface Management
Although the Attack Surface may seem vast and unmanageable, there are plenty of procedures, policies, and controls that can be put in place to mitigate the risks that come with the Attack Surface.
How Can You Protect Yourself?
Asset Management
As an organization, it is important to understand where your assets lie, and who is in possession of the asset(s). This is true for both physical and digital assets. You will want to establish an asset tracking and management system for your physical assets, and a data governance, discovery, and identification solution for all digital assets.
End-User Cyber Awareness Training
Despite all policies, procedures, and security tools that may be in place within your organization; there is still one attack vector that is always a reliable choice for cybercriminals: your employees.
Cybercriminals are more frequently leveraging human emotion and psychology to execute social engineering attacks as an easy entry point to your systems, accounts, and networks.
One way to attempt to prevent these types of threats is to train your employees on common practices that will lessen the likelihood of a social engineering attack. Cyber awareness training can help make your employees aware of the social engineering methods used to commonly take advantage of users.
Phishing tests are commonly used to supplement cyber awareness training to provide real-world examples of phishing emails without any risk. These phishing campaigns will report which users open the emails and/or enter their credentials.
How Can Alliance InfoSystems Help?
Risk Assessments
Alliance InfoSystems can perform risk assessments against your organization and assign risk scoring to the individual aspects of your organization.
Once a risk assessment is performed, the results are reviewed, and any remediation steps are determined. Once the necessary remediation items are determined, a Plan of Action is developed with a severity score assigned to each remediation item, to help determine a method of prioritizing all remediation items.
Vulnerability Assessments
Alliance InfoSystems is able to perform internal and external vulnerability assessments against your systems and networks. Understanding where your internal and external vulnerabilities may lie will help protect against exploitation in the future and will provide a better understanding of what areas of your security posture may need immediate attention.
MSSP Services
With Alliance InfoSystems’ Guardian Network Protection Services (GNPS), all aspects of your security stack will be covered, and our team of security engineers respond in real-time to cyber incidents that may impact your organization. In addition to real time response, weekly reporting will provide insight into your security environment.
Windows & Third-Party Patch Management
AIS’ Remote Monitoring and Management (RMM) solution provides weekly managed patching deployments to all of your workstations and servers for all Windows and third-party patches, in addition to centralized software deployment, scripting and automation, and full remote management.
Managed Anti-Virus and EDR
Our behavior based anti-virus and Endpoint Detection and Response (EDR) solution is able to automatically kill and quarantine malicious files, with the full ability to quarantine and whitelist in the event of a false-positive. In addition to anti-virus and EDR, vulnerable applications are shown to allow for immediate patching.
Managed APT/Malware Detection
Our Advanced Persistent Threat and malware detection solution has a full team of 24×7 security engineers who are able to immediately respond to malware incidents within your organization.
Endpoint Policy Management
AIS’ endpoint policy management solution makes it easy to immediately enable or disable policies for your systems. These policies range from password complexity enforcement to creating hidden ransomware canary files that are able to alert on modification. These policies can be reviewed with your operations staff and tuned to work best with your organizations systems and applications.
DNS Filtering and Protection
Filtering at the DNS level is done both at the endpoint level and at the network level to prevent any connections to unwanted or malicious websites. Our DNS filtering solution is also able to provide reporting into top blocked connections to provide better insight into your organization’s web safety.
24×7 Security Monitoring
Our 24×7 security monitoring solution is able to monitor all of your organization’s workstation and server logs, processes, services, installed software, and behavior to alert on any activity that may indicate a security incident. In addition, your Microsoft 365 environment will be monitored for any unwanted log ins or risky user behavior.



