Can you spot the difference? AInfosys.com vs Alnfosys.com
Many people here would not notice that the first one has a capital “i” whereas the second one has a lowercase “L”. This method of exploitation is known as Typosquatting and is something that many cybercriminals are using to their advantage.
A cybercriminal may take advantage of this by registering these slightly modified domain names and performing different methods of cyber-attacks.
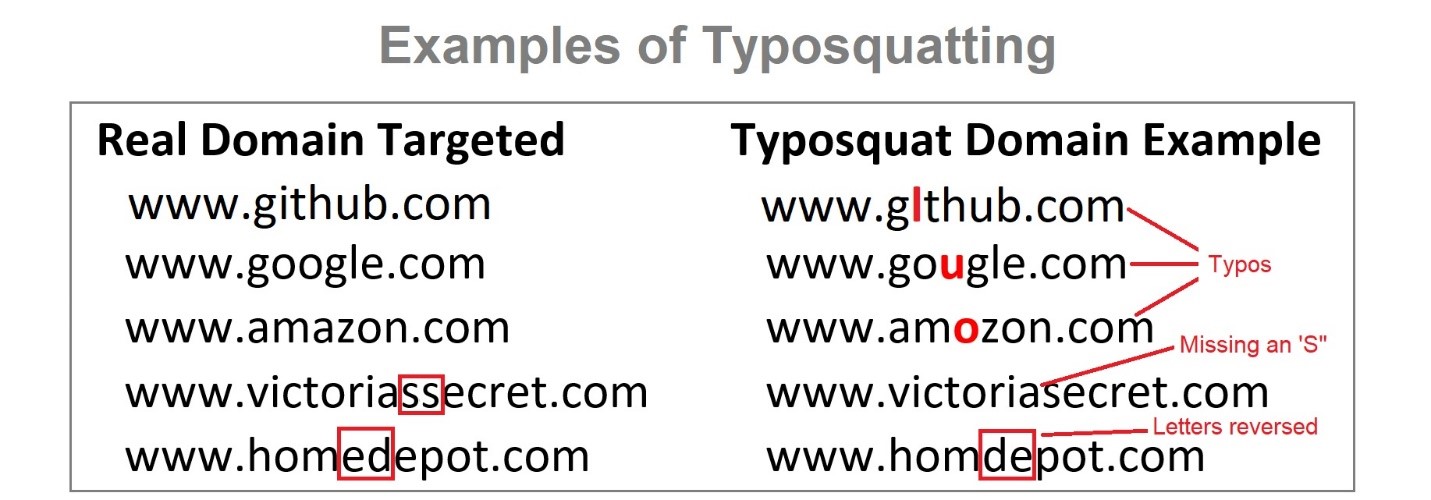
Research shows that the brain will attempt to correct a mixed message using the message’s context clues. Typosquatting relies on this fact and takes advantage of the user’s inability to notice slight differences between legitimate domains and lightly modified domains.
See the following examples of domain names that have been slightly modified to appear to be the legitimate domain:
What Can Go Wrong?
Why is it so bad to accidentally mistype the URL and go to the incorrect site?
There are several ways a malicious user can set up the site to attack you.
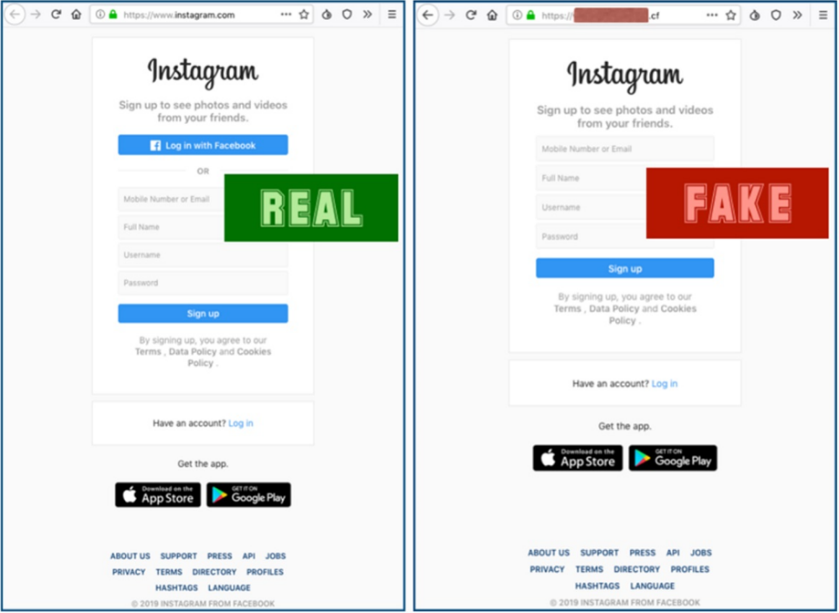
The first purpose of this attack is to rely on the user mistyping the spelling of a website, where they may be taken to a different malicious website. For example, a user may have the intention of typing “Instagram.com” and pressing the ‘Enter’ key, but they had inadvertently typed “Instagram.cf” and pressed the ‘Enter’ key.
The attacker could make the malicious site look identical to the legitimate site, to have the user enter their credentials, which are then sent to the attacker. One security control that may help protect after falling victim to this attack is Multifactor Authentication or MFA. Even if the attacker has your username and password, they may still be restricted from getting into your account if you have two-factor authentication enabled.
Another way that these websites can be set up to attack you is with malware. When a domain name is mistyped, you may be directed to a website containing malicious links. The website may even contain scripts that cause malware to immediately download to your PC; so even if you immediately realize you are at the wrong website and close the window, you have already downloaded the malware.
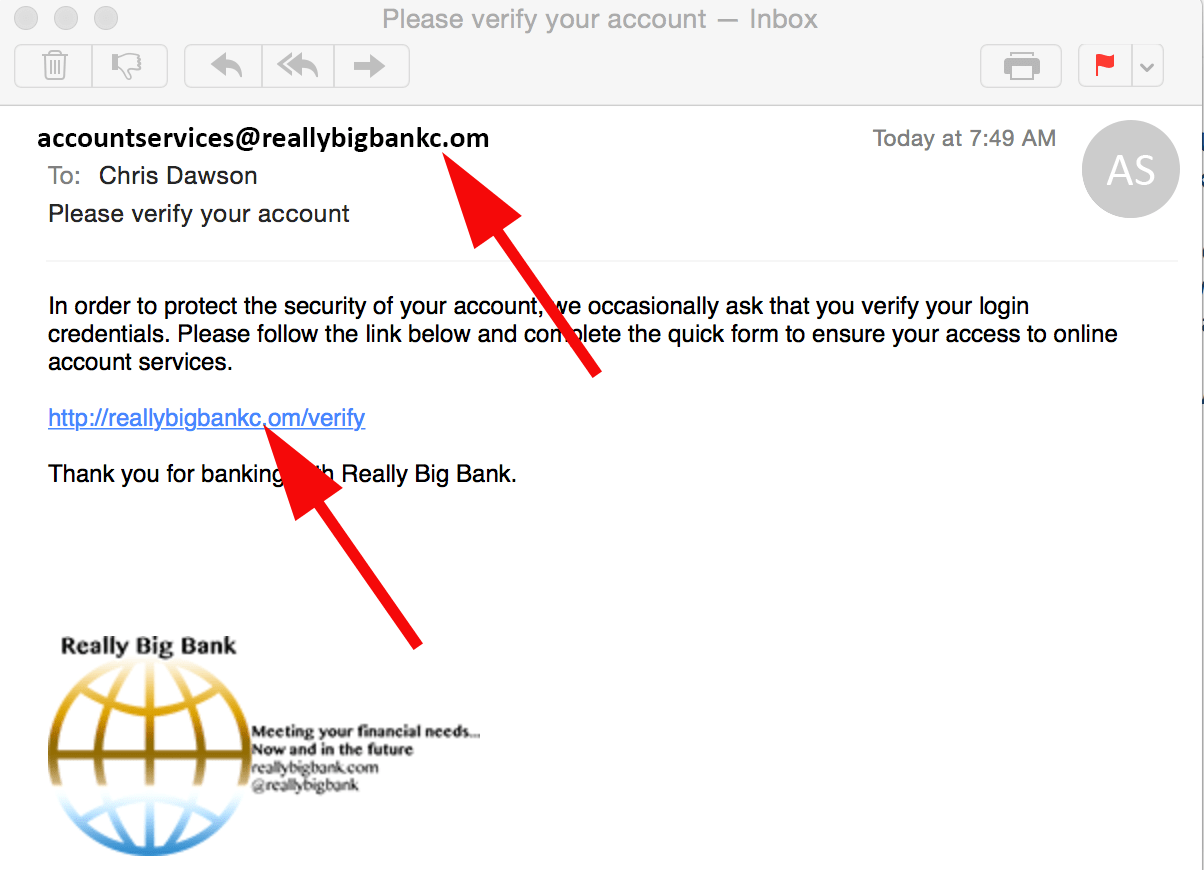
Finally, these fake domains may be purchased by cybercriminals, configured to send, and receive an email, and used in an email phishing attack. See the first example from this article: AInfoSys.com vs AlnfoSys.com. An attacker may take advantage of this and send emails within the organization posing as management or executive staff. This may cause an increased sense of urgency and increase the likelihood of employees responding to or opening malicious emails or malicious links within phishing emails.
Source: https://www.proofpoint.com/us/threat-insight/post/Attackers-Increasing-Use-Of-Typosquatting
How Your Business is Affected
How does this affect your company?
The effects of a typosquatting attack can range from financial damage to information or data being stolen, or even reputational damage to your organization.
For example, WellPoint, now known as Anthem. WellPoint is a health insurance company. A few years ago, several of WellPoint’s customers fell victim to a phishing attack using a typosquatting URL. The fake domain was www.we11point.com where the “L”s were replaced with “1”s. This clearly hurts the company’s image from their customers because they were hacked even though the company had nothing to do with the phishing or the fake domain name.
What AIS is Doing to Help Protect Against Typosquatting
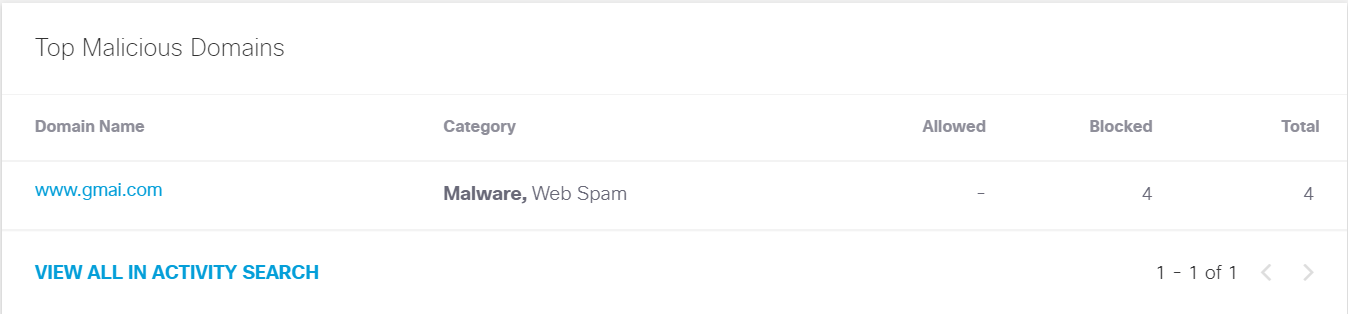
Alliance InfoSystems has several solutions to counteract typosquatting. Our Guardian Network Protection Services (GNPS) security stack offers DNS filtering and protection, which prevents users from inadvertently browsing malicious sites. As you can see, our DNS filtering solution was able to prevent a user from inadvertently browsing to www.gmai.com versus the intended website, www.gmail.com.
Alliance InfoSystems also offers security controls in the event an organization does fall victim to a successful typosquatting attack. Multifactor Authentication (MFA) is offered, to protect user’s accounts and systems in the event of a credential breach. Alliance InfoSystems has full centralized management of your organization’s MFA environment, providing insight into unwanted authentication attempts.
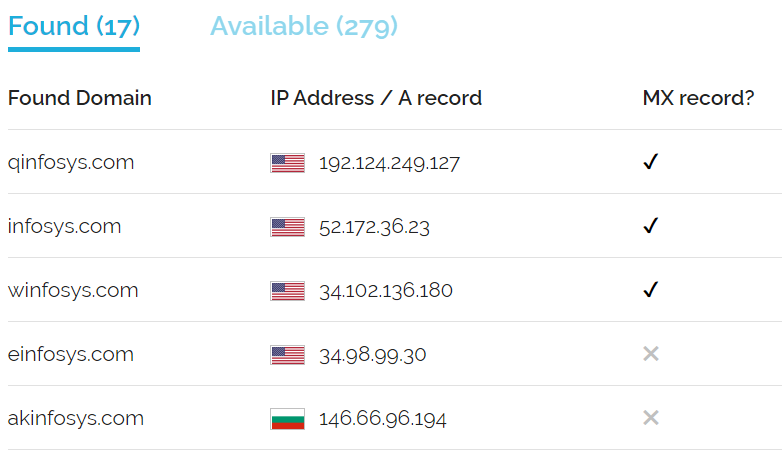
We also provide a service that will search for any registered domains that are similar to your organization’s domain, and whether they have an MX DNS record associated with the domain, which means they may be using the domain to send or receive email.
The example below will show some results for the ainfosys.com domain.